Changing Timestamps To Disguise Malware
This week we look at file timestamps, what they are, what they mean, and how bad actors can use them to their advantage when compromising sites. Timestamps can be a good clue as to what happened if a site was compromised. But are timestamps foolproof? Let’s find out what they are and see.
What Is A Timestamp?
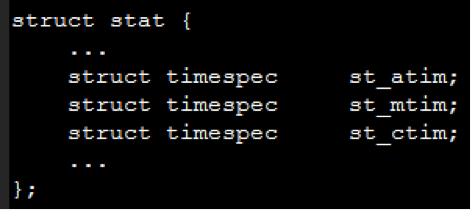
Timestamps are POSIX standard times associated with an inode, or file, on a Unix file system. Timestamps are retrieved with the stat() system call, and the files that define the data structure that contains the timestamps, on Ubuntu for example, are /usr/include/i386-linux-gnu/sys/stat.h on 32-bit systems and /usr/include/x86_64-linux-gnu/sys/stat.h on 64-bit. With the other file attributes removed, the stat struct for timestamps looks like this.
The three times shown in the struct, st_atim, st_mtim, and st_ctim, are the atime, mtime, and ctime associated with files. The times represent:
- The access time, which is the last time the file was accessed, i.e. read
- The modification time, which is the last time the file was modified, i.e. edited
- The change time, which is the last time the file was changed, including an edit, ownership change, or some other file change
How A Timestamp Works
To see timestamps in action, we can use an FTP client like FileZilla and view files’ modified time. We can use the ‘ls’ command on Linux with some choice switches (man ls) to view the times. Or we can use the ‘stat’ command to see every timestamp and more.
$ stat asdf
File: ‘asdf’
Size: 0 Blocks: 0 IO Block: 4096 regular empty file
Device: 801h/2049d Inode: 265176 Links: 1
Access: (0644/-rw-r--r--) Uid: ( 1000/ user) Gid: ( 1000/ user)
<strong>Access: 2015-10-14 14:33:17.957053885 -0700
</strong><strong>Modify: 2015-10-14 14:33:17.957053885 -0700
</strong><strong>Change: 2015-10-14 14:33:17.957053885 -0700
</strong>Birth: -
Here we can see the file was accessed, modified, and changed around 2:30 pm. Depending on the system, the stat command may show birth, or creation, time, though it’s not standard across systems. Now let’s edit the file and run the ‘stat’ command again.
$ nano asdf
$ stat asdf
File: ‘asdf’
Size: 5 Blocks: 8 IO Block: 4096 regular file
Device: 801h/2049d Inode: 265176 Links: 1
Access: (0644/-rw-r--r--) Uid: ( 1000/ user) Gid: ( 1000/ user)
<strong>Access: 2015-10-14 14:35:15.629055286 -0700</strong>
<strong>Modify: 2015-10-14 14:35:17.829055312 -0700</strong>
<strong>Change: 2015-10-14 14:35:17.829055312 -0700</strong>
Birth: -
Here you can see the two seconds it took to access, edit, and save the file.
The Touch Command
So we’ve seen how editing a file changes timestamps. How can we change the timestamp without editing the file? One way is to use the ‘touch’ command, which changes the timestamps and leaves the file contents intact.
$ touch asdf
$ stat asdf
File: ‘asdf’
Size: 5 Blocks: 8 IO Block: 4096 regular file
Device: 801h/2049d Inode: 265176 Links: 1
Access: (0644/-rw-r--r--) Uid: ( 1000/ user) Gid: ( 1000/ user)
<strong>Access: 2015-10-14 14:46:14.449063127 -0700</strong>
<strong>Modify: 2015-10-14 14:46:14.449063127 -0700</strong>
<strong>Change: 2015-10-14 14:46:14.449063127 -0700</strong>
Birth: -
All three timestamps were changed and the file size stayed the same. Now the important question, how could a bad actor change timestamps of malicious files written or uploaded to a compromised site to hide them?
If an adversary had command line access – and let’s hope they don’t – they could use a custom touch command to define a timestamp more inline with existing files on the system.
Using the ‘man touch’ command, we see there’s a ‘-t’ switch which takes a single argument of a timestamp of our choosing.
$ man touch
...
-t STAMP
use [[CC]YY]MMDDhhmm[.ss] instead of current time
Let’s change the timestamp of our file to something more festive, say Halloween from last year.
$ touch -t 201410312200 asdf
[~]$ stat asdf
File: ‘asdf’
Size: 5 Blocks: 8 IO Block: 4096 regular file
Device: 801h/2049d Inode: 265176 Links: 1
Access: (0644/-rw-r--r--) Uid: ( 1000/ user) Gid: ( 1000/ user)
<strong>Access: 2014-10-31 22:00:00.000000000 -0700</strong>
<strong>Modify: 2014-10-31 22:00:00.000000000 -0700</strong>
<strong>Change: 2015-10-15 10:28:16.429907264 -0700</strong>
Birth: -
We can see all three timestamps changed. Two of them, access and modify, changed to our haunting time. The third, change, changed to the time we ran the touch command. This is significant because most ways people view timestamps, like ‘ls -l’ or FileZilla, only show the modified time of our chosen witching hour.
Malicious Use Of The Touch Command
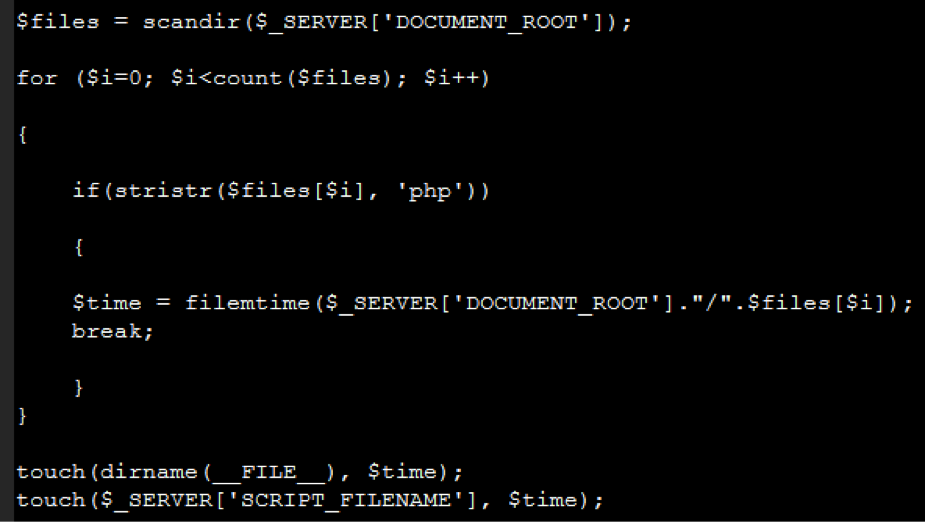
Now, back to the web. Let’s look at some timestomping (the term for maliciously changing timestamps) code we recently found in PHP malware uploaded a compromised site.
The code makes a list of all files in the current directory, takes the modification time of the first PHP file it finds, and changes the modified time of itself and the directory it’s in. Sneaky. This small step can go a long way to camouflage malicious files, as most people view files though a file browser or FTP client.
What do you as a security-conscious site owner do about timestomping? Using SiteLock INFINITY or other SiteLock scanning solutions obviates the issue for you – you won’t have to worry about it. SiteLock has multiple ways of detecting malware, and if it comes to it, we take timestamps with a big grain of salt.
Call 855.378.6200 to talk with one of our consultants about putting together a custom website security solution.