Analysis Of An SEO Spam Campaign
Search engine spam, more frequently known as SEO spam, is a technique used to manipulate rankings in a way that is not allowed by search engine terms of service.
This week we’ll take a look at an interesting SEO spam campaign that recently came across the SiteLock research desk. Turkish escorts are apparently big business and we had the opportunity to dig a bit into the makings of a malicious Turkish escort spam campaign.
Our analysis began with a malicious PHP file, /images/2ndex.php, which was likely uploaded to the victim site. It contained, along with an uploader, a line of code using a system command, wget. This command’s purpose was to retrieve another PHP file located at a Luxembourg domain, http://www.inmediasres [dot] lu/tmp/sym/weba1.php.

System wget
In the image below, you can see that the file named weba1.php wrote FOPO-encoded PHP to the index.php file on the infected site. FOPO stands for Free Online PHP Obfuscator, an online tool that can be used to make malicious code more difficult to find in a file. In the malware image below, note that dizin and dosya mean directory and file respectively in Turkish.

File hacker
The FOPO code decoded to a modified Joomla! index.php file with an interesting bit at the end. The SiteLock research team beautified the code for readability, as shown in the image below.

Injecting links
The interesting bit of this SEO spam malware is the search engine bot detection that is included in the code. This triggers the injection of a file_get_contents() of a base64 encoded URL. The base64 code is decoded to the following url: http://www.ilerigel [dot] com/website.php?page=6. This page, when loaded, then injects a hidden paragraph of Turkish escort links into the existing website code.

Changing the query string on the url, from page=6 to page=7, yielded similar and more voluminous results.

Page=7
After a smidge of URL manipulation and a hint of cURL, all of the escort links found were harvested and written to text file.
We decided to dig a little deeper. The Luxembourg domain seemed to be hacked as there was a sign of a sym link, a common malware tactic, along with a web-based file manager, and the site runs an older version of Joomla!, 1.7. Google also shows escort spam in search results for the domain.

Malicious files

Joomla 1.7!

Search results
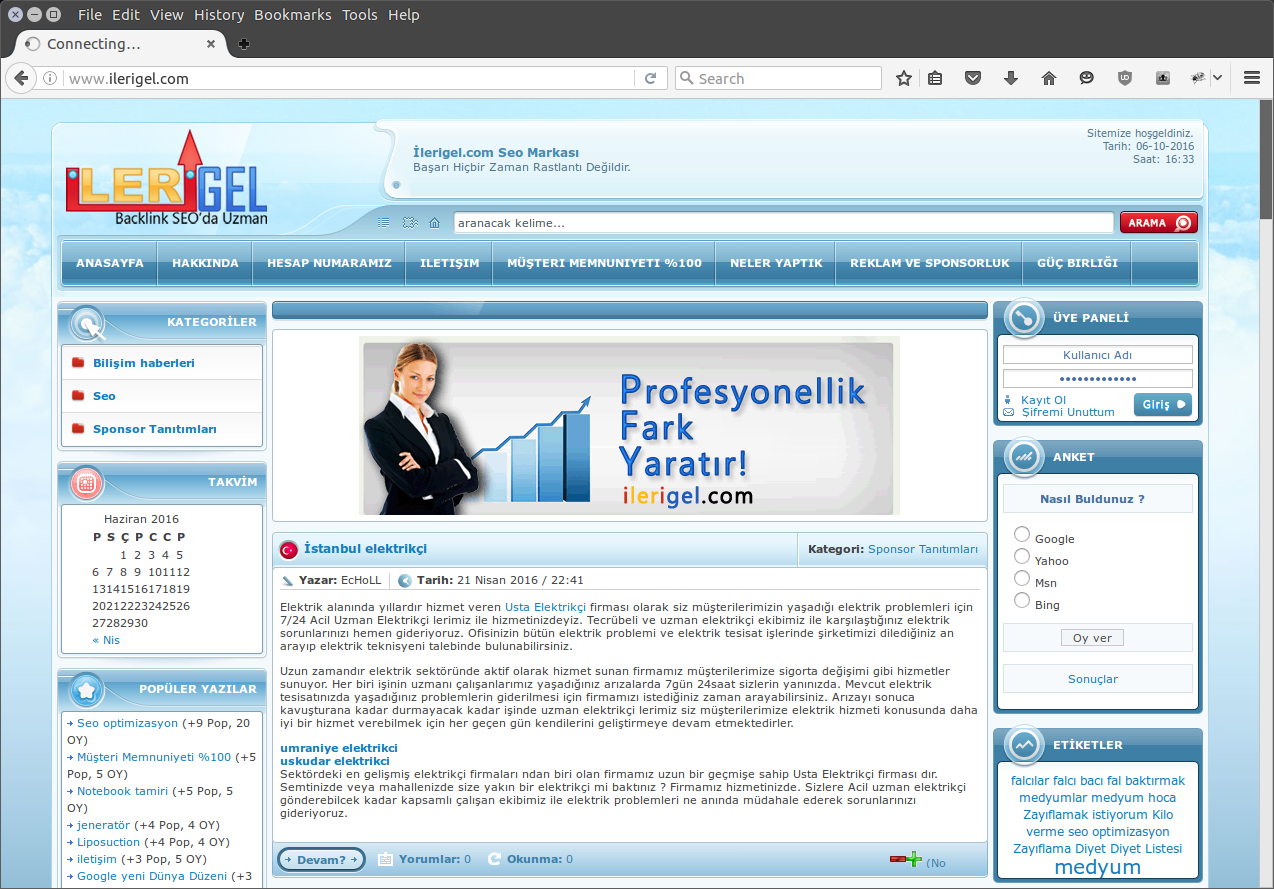
Ilerigel [dot] com however did not seem compromised. The links seemed purposefully hosted and the site itself offers SEO services: Backlink SEO’da Uzman, or Backlink SEO Expert.
![Ilerigel [dot] com](https://blog.sitelock.com/wp-content/uploads/2016/06/turkish-escort-spam-04.png)
Ilerigel [dot] com
The strongest indicator that ilerigel [dot] com is purposefully hosting the malicious SEO spam links is the admin email address from the domain’s WHOIS record, admin@ankaratrescort [dot] com. At this point we thought best to conclude the analysis.
![admin@ankaratrescort [dot] com](https://blog.sitelock.com/wp-content/uploads/2016/06/turkish-escort-spam-20.png)
admin@ankaratrescort [dot] com
Regardless of the type of spam infection — pharmaceutical, sneaker, or otherwise — SiteLock’s scanners detect SEO spam infections and SiteLock’s SMART technology can automatically clean them. Please visit SiteLock’s plan page to view our the services we offer, or call (855) 378-6200 for more information.





